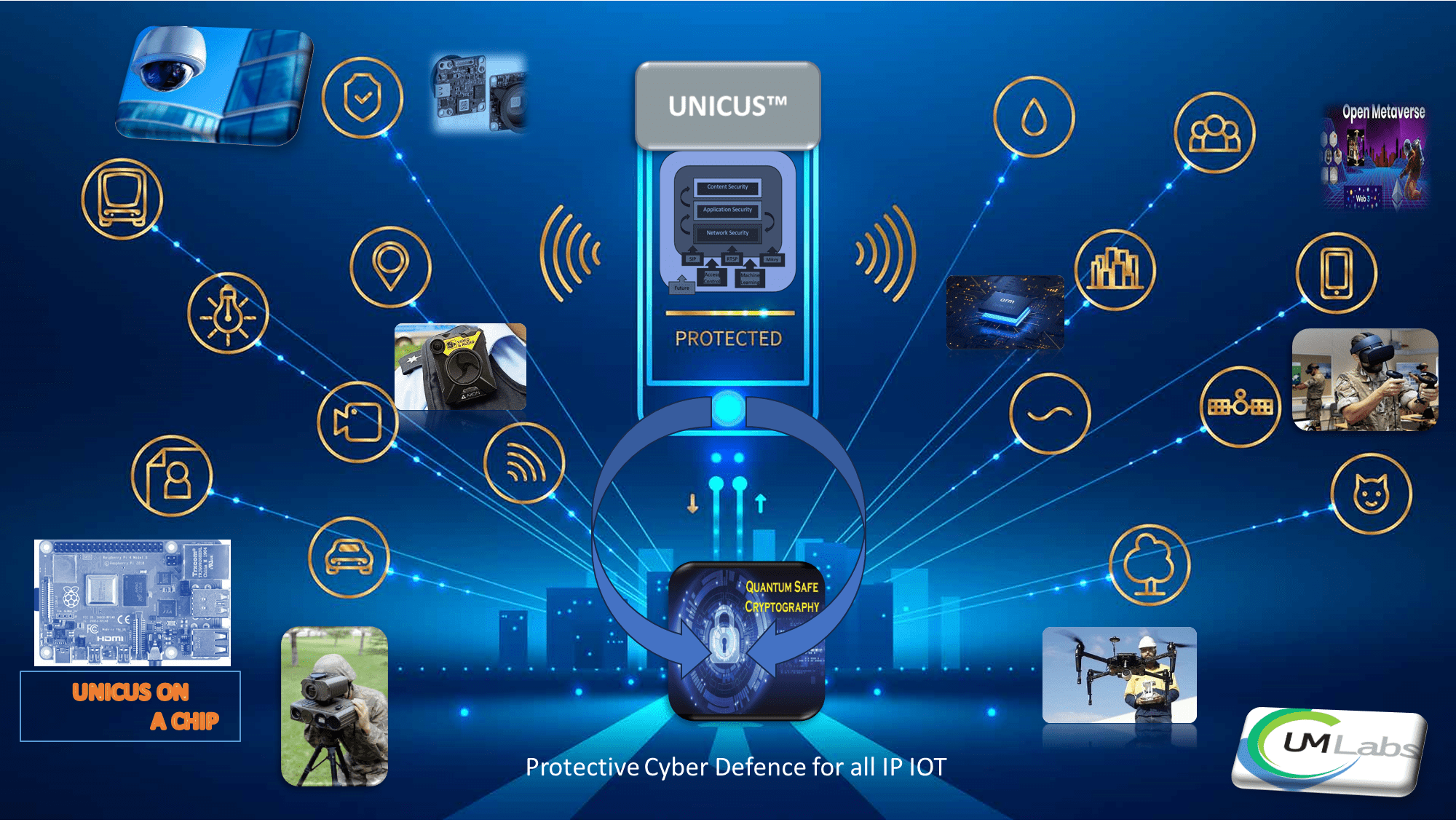
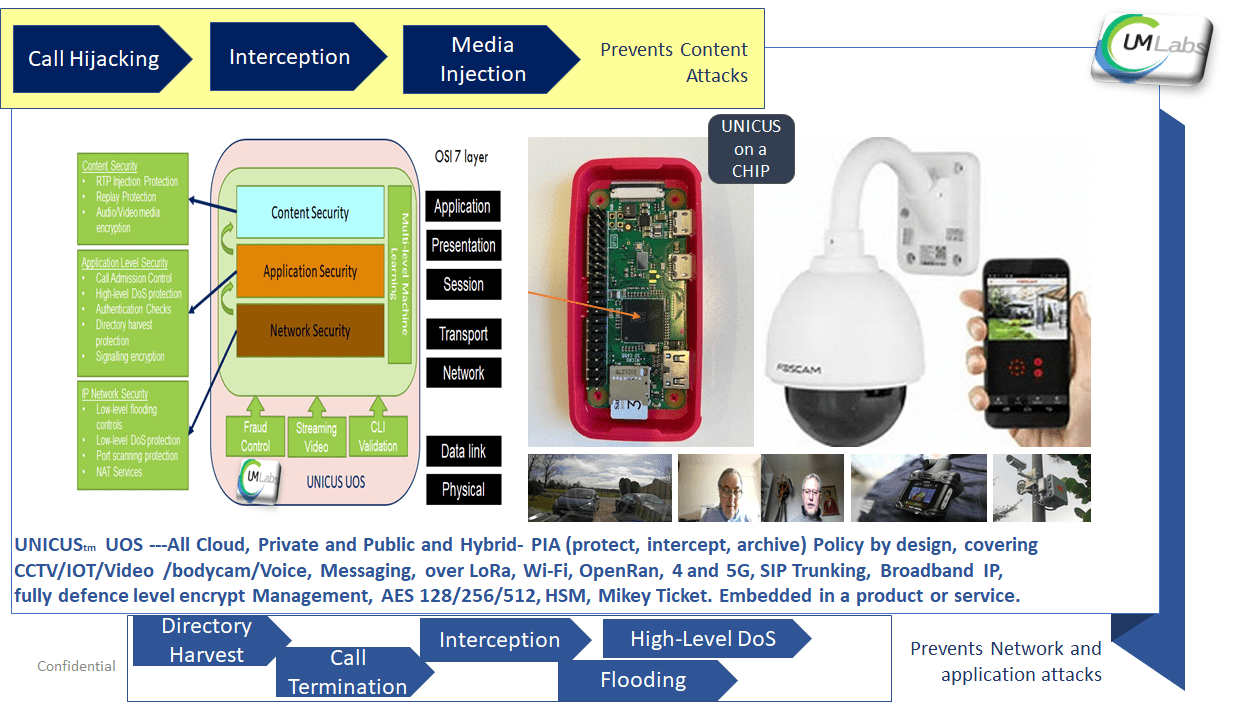
UM-Labs R&D joins Innovation Martlesham at BT Adastral Park.
UM Labs R&D joins the Innovation Martlesham Ecosystem at BT Adastral Park (USA Parc in a UK design) and are pleased to have joined with the ability to test and prove the advanced R&D designs against all IP networks. UM-Labs are looking forward to working closely with other members of