Call fraud is a problem that all phone systems face. Moving service delivery to IP networks enables fraudsters to use automated tools to identify vulnerable systems and to exploit those systems by making fraudulent calls, leaving the victim organisation to meet the cost.
UM Labs in conjunction with ITSPA developed SNITCH to combat call fraud. SNITCH identifies the sources of fraudulent calls enabling UM Labs R&D’ Unicus UOS to protect systems by blocking those sources.
The data collected by SNITCH shows that most attackers take a simplistic approach, using SIP over UDP in their attacks. UDP provides a connectionless, unencrypted network transport and is the default setting for most phone systems. SIP also runs over TLS, an encrypted transport protocol use by many web sites. Until recently, simply switching from UDP to TLS would have protected a systems from most fraud attacks and provided obvious other benefits.
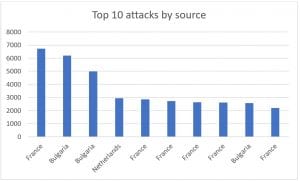
At least some fraudsters are getting smarter, the logs on UM Labs’ own phone system show that in the 12 days since the beginning of August fraudsters made 100,963 attempted calls using SIP over TLS. Every one of these attacks was identified by SNITCH and blocked by Unicus.
The 100,963 attacks originated from 119 different sources, the 10 most active source are all in Europe.