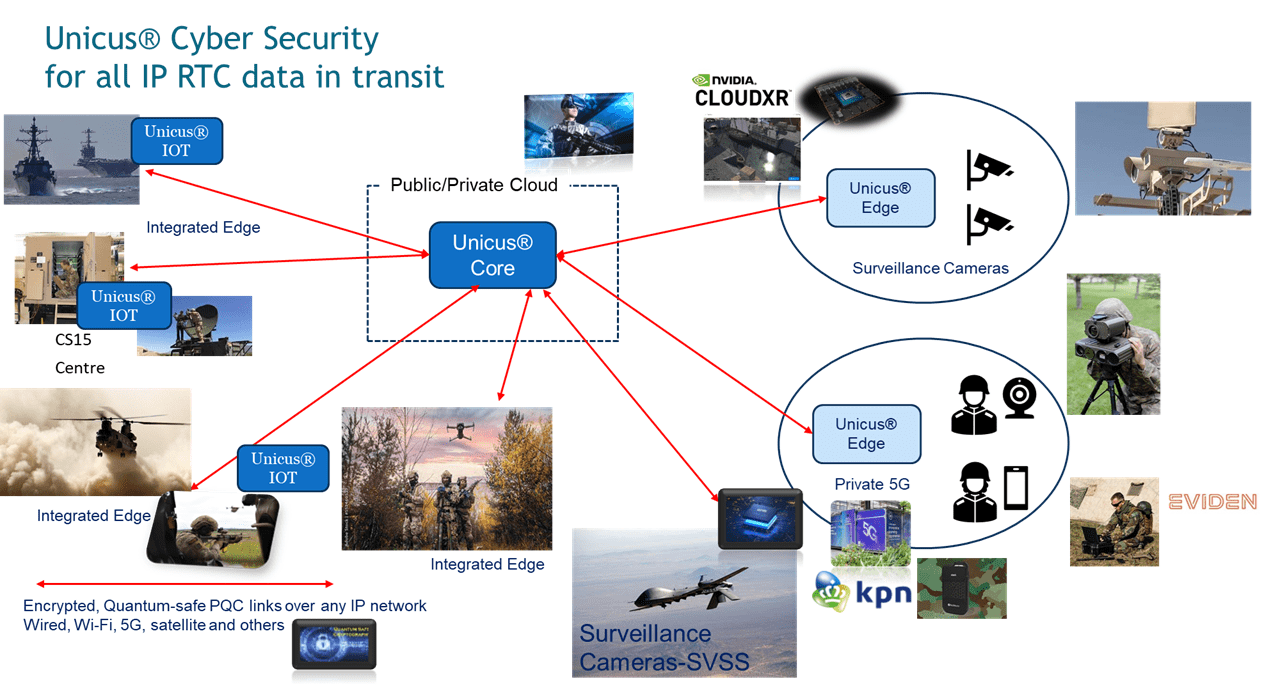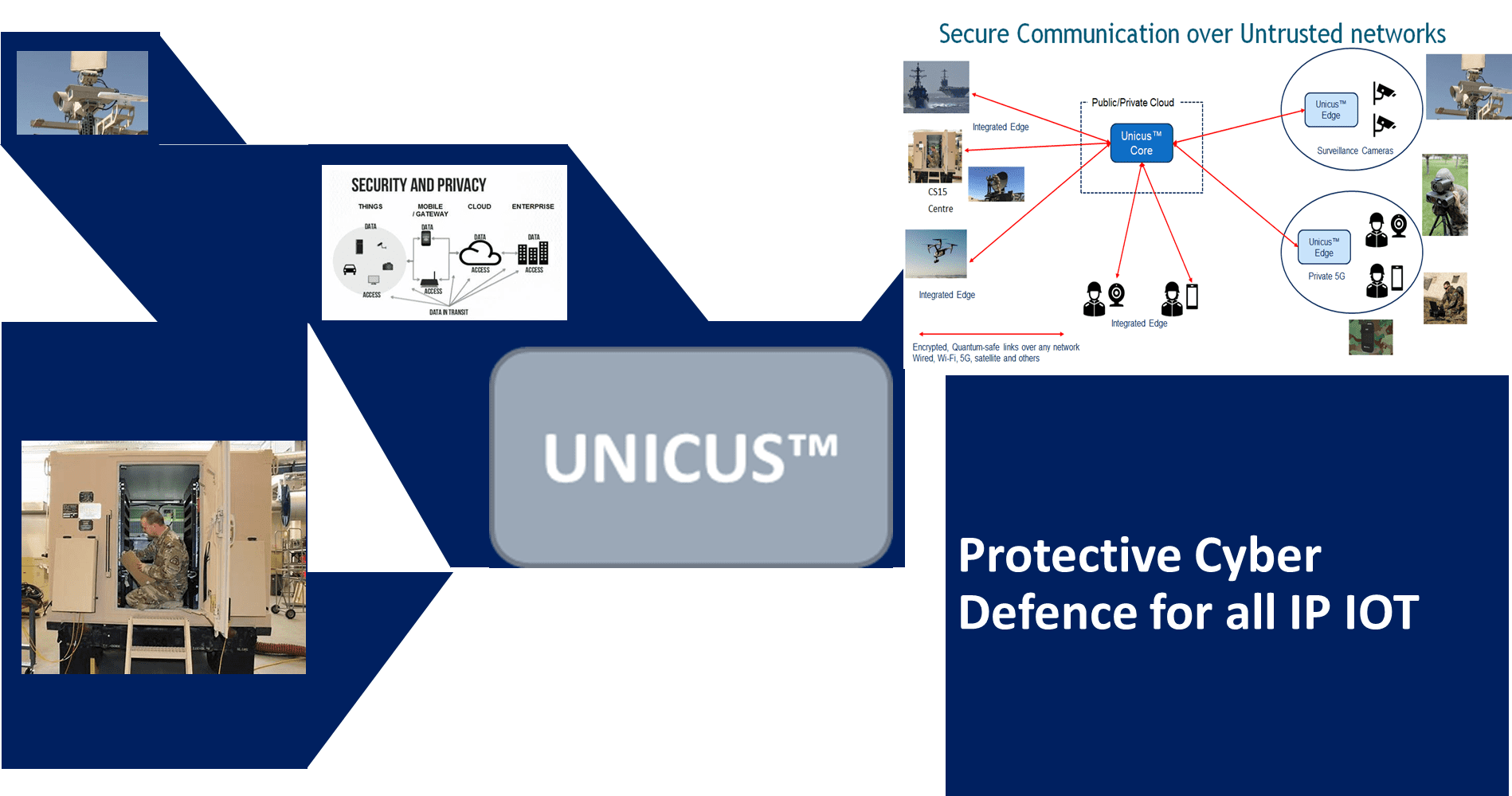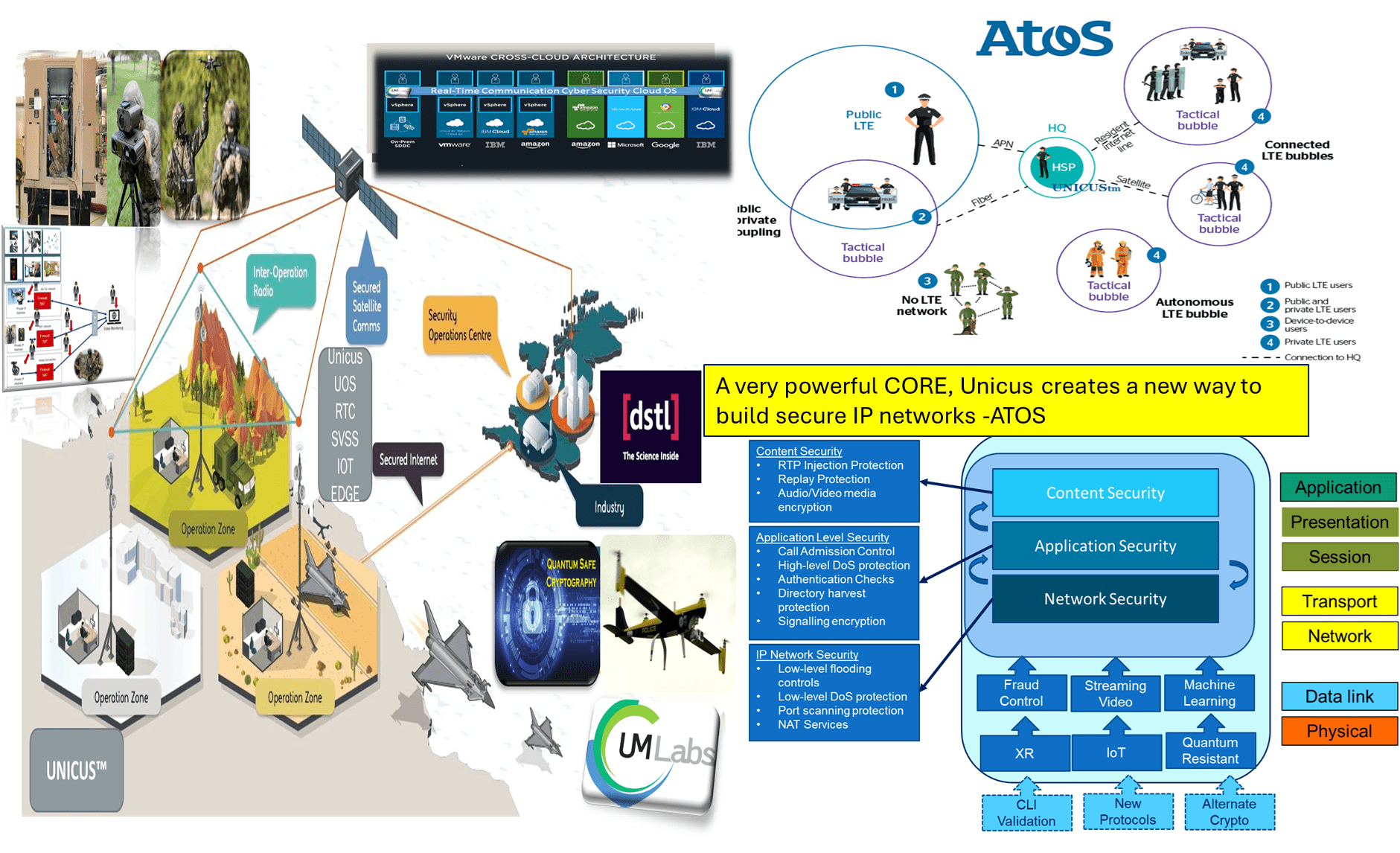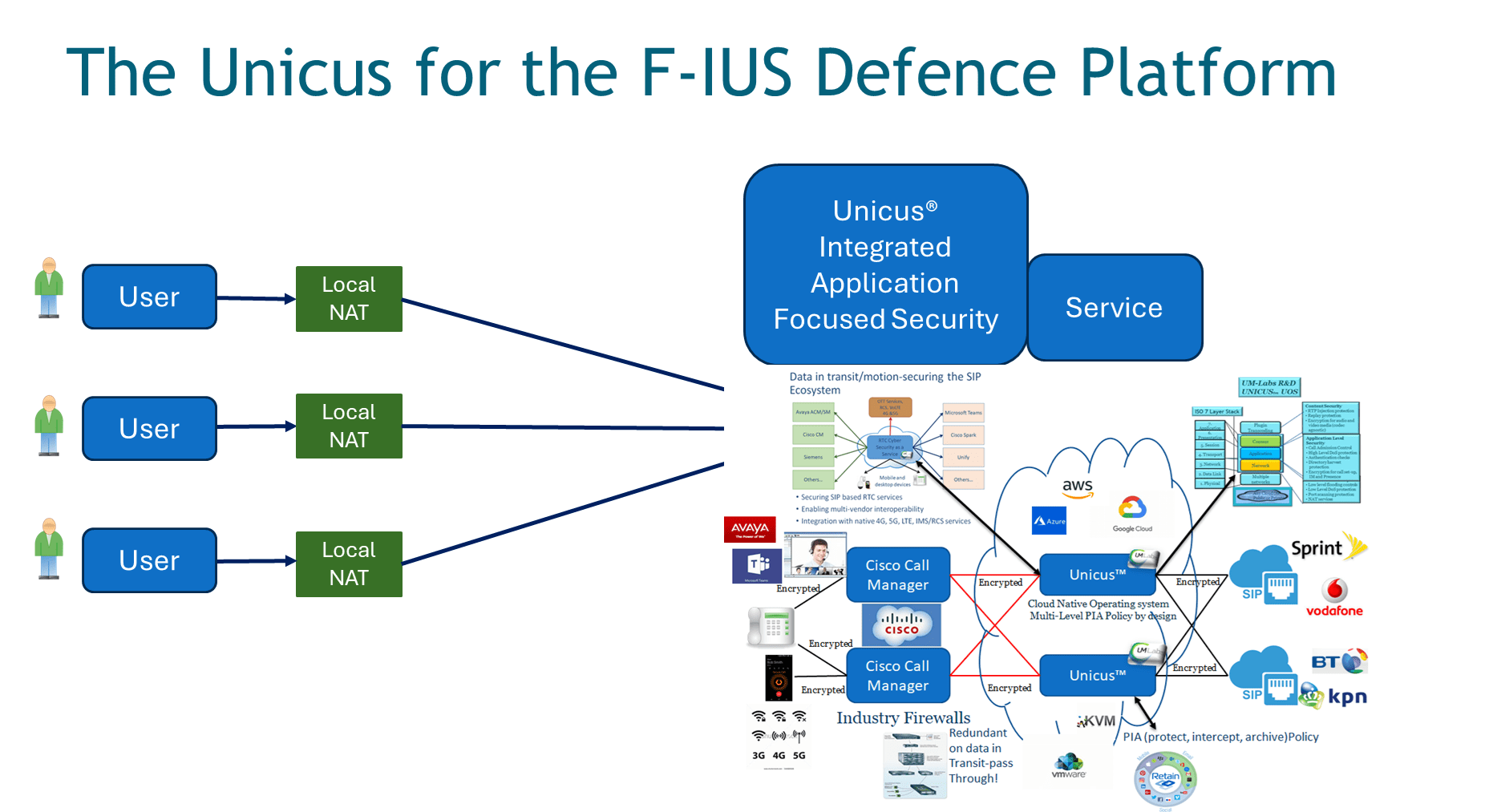
Peter Cox, Inventor and CEO at UM-Labs R&D has moved LEM-AI to the next level, hear about this first hand at the AI -World Congress in London on the 19th June 2025
As cyber threats increasingly target real-time communications and grow ever more sophisticated, traditional security measures are no longer sufficient. The UM-Labs AI Large Event Model (LEM) introduces a revolutionary approach to cybersecurity for real-time traffic by leveraging AI-powered threat detection, predictive intelligence, and automated response mechanisms. With over a decade’s