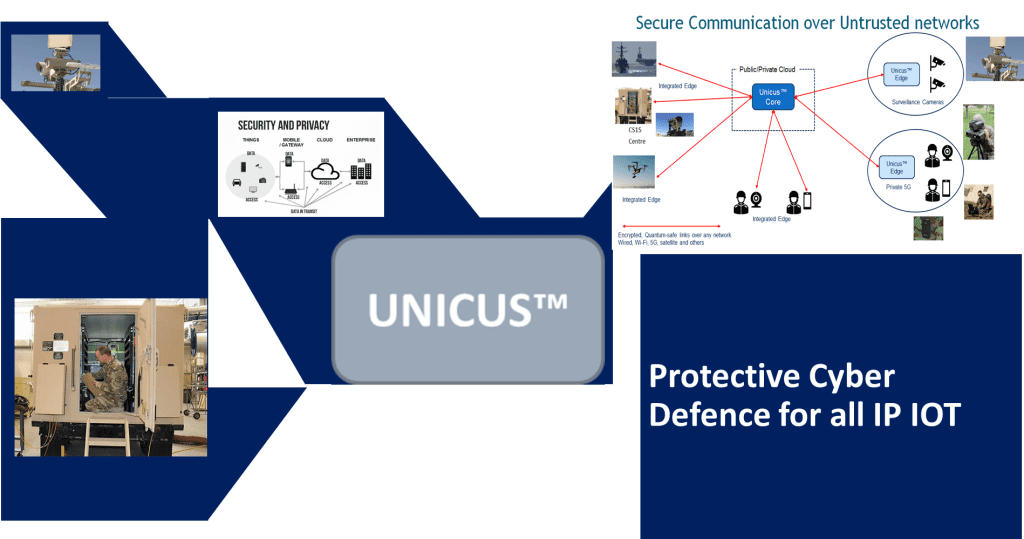
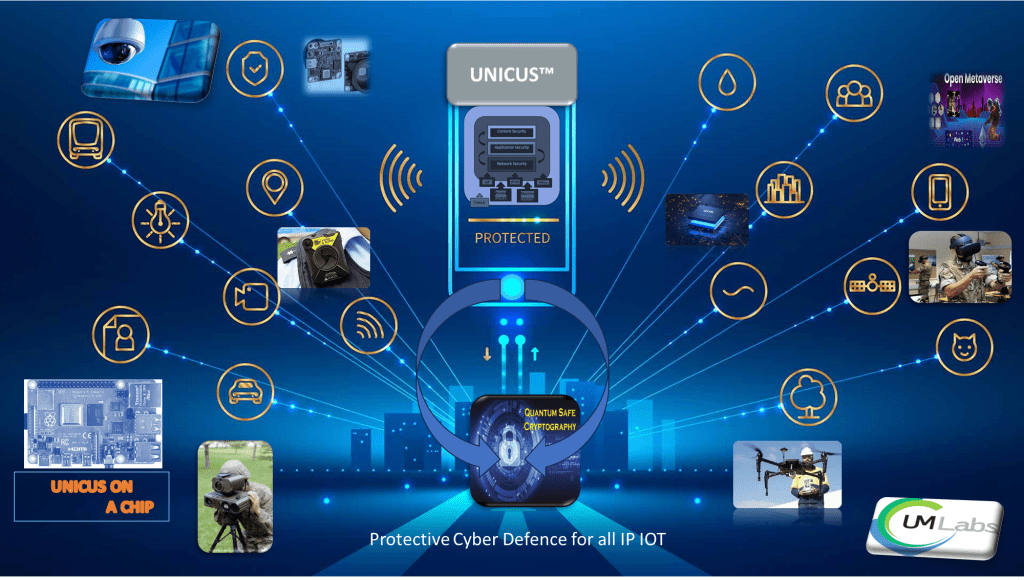
‘Secure by default’ with Cybersecurity for the Internet of Things, licence the innovation technology and build a service or embed in an EDGE device with the system on a chip toolkit sponsored by the UK DSTL.
The Internet of Things, IoT, describes the use of IP networks to interconnect a range of devices providing monitoring and response services and to connect those devices to a central control point. In common with all interconnected devices and services using IP networks, IoT devices, the control systems and the communication between them is at risk of attack. While some of the threats facing IoT networks are shared with other IP services and applications, the architecture of IoT systems exposes those systems to a set of threats which can only be countered with countermeasures designed specifically to address the IoT specific threats.
This document describes how Unicus™ IoT provides a foundation for building and deploying secure IoT networks.
Secure by Default